Curiosity is one of the things that drives humanity further. It is this trait that has led to some of the greatest inventions.
Here at Gradient Cyber, we want to empower our customers to know more about what is happening inside their environment. Amongst many other valuable insights we already provide, we’ve added the ability for them to send our way suspicious documents, files or other artifacts that require further analysis.
The process is straightforward, we only require a brief description of the uploaded artifact (how it was obtained, where it was found, or any other information that could help us during our investigation.)
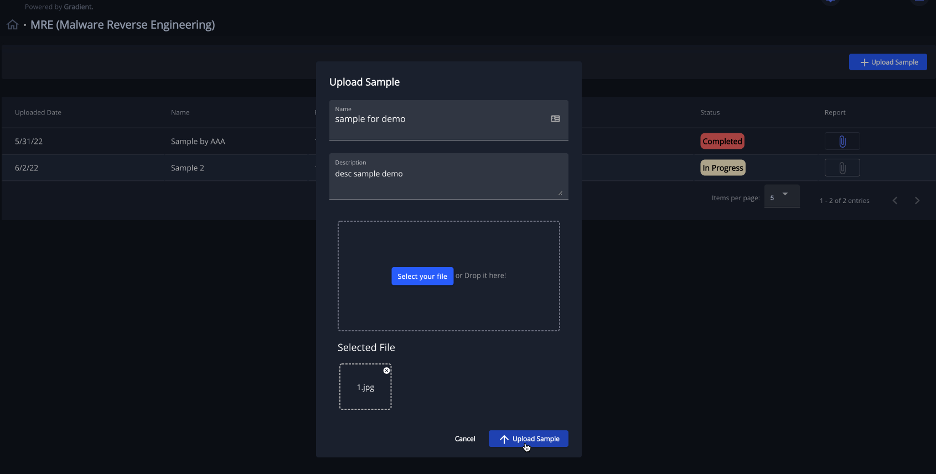
Due to the possible malicious nature of the suspicious sample, we require that the file is archived inside a .ZIP or .7z password protected archive, and we are asking our customers to use a standard password – the word suspicious.
This way we make sure that whoever is going to analyze the sample will know how to extract it from the archive.
Inside our app, the customer has access to see a collection of uploaded samples and download the report about each sample.
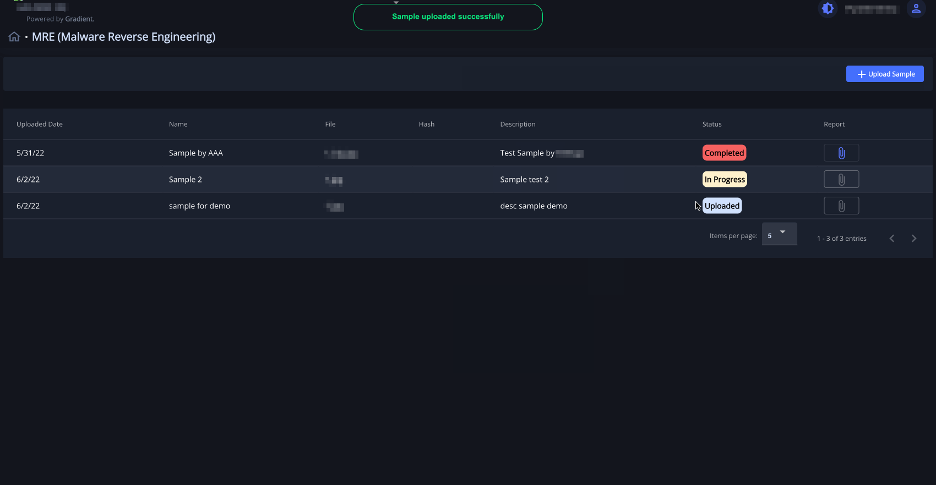
Also on our end, the app is easy to interact with it – we can view and download the samples and upload reports.
The report includes detailed information about the sample file and the conclusions of the analyst that performed the investigation. If available, recommendations for further actions could be included in the report, based on the investigation outcome.
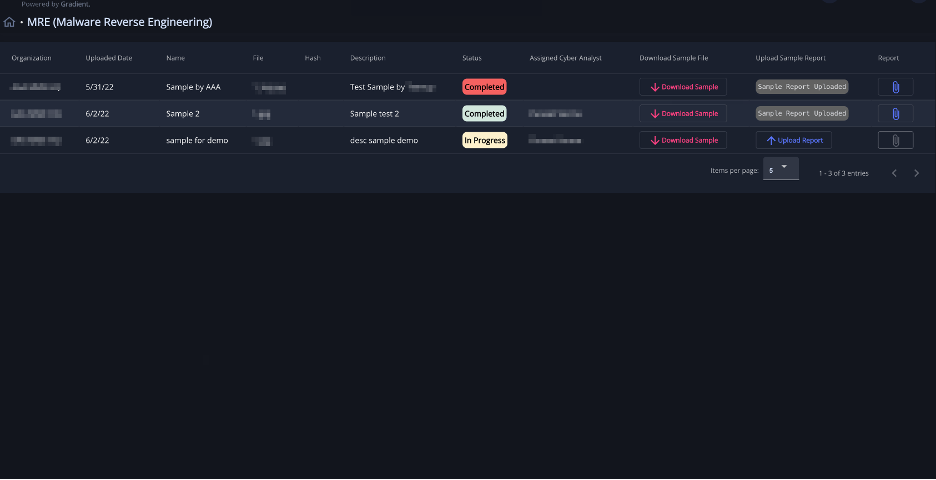
We color coded the status field for each sample, so that is easy to spot the samples identified as malicious – those are marked Completed, whereas for FPs we use Completed.
During our investigation we perform both a static and a dynamic investigation for samples that require it, using specific tools and environments.
My name is Razvan Cristea and I’m a Cyber Security Analyst. I joined the Gradient Cyber team in February 2020 where I work on multiple projects, and I am the pioneer for the Malware Reverse Engineering project. My goal is to use my experience gained here and during my passionate journey (CTF events, challenges on SANS and other renowned websites and hours of analysis) to provide feedback on suspicious artifacts found in our customer’s infrastructure.
In this blog, we thrive to publish findings from our investigations and analysis and join the community of cybersecurity researchers, sharing knowledge and giving others the eagerness to join us in this beautiful journey.




