In today's interconnected digital landscape, organizations face an ever-growing range of cybersecurity challenges.
With their deceptive tactics and sophisticated approaches, cybercriminals cast their nets wide, targeting unsuspecting individuals within organizations to gain unauthorized access, steal sensitive information, or deploy malicious software.
In recent years, phishing attacks have become increasingly prevalent, evolving in sophistication, and posing significant risks to organizations' integrity, data security, and financial stability. These cyber threats are not only confined to large enterprises but also affect small and medium-sized businesses, highlighting the urgency for heightened vigilance across the board.
Phishing emails are deceptive messages that appear legitimate, often mimicking well-known companies, trusted individuals, or recognized institutions. The perpetrators employ various social engineering techniques, leveraging psychological manipulation to trick recipients into divulging sensitive information, such as passwords, credit card details, or access credentials. Alternatively, they may entice recipients to click on malicious links or download infected attachments, thereby infecting computer systems with malware or ransomware.
Is it you I’m looking for?...
Recently, I came across an email in my personal inbox supposedly sent by a reputable car dealer, which included an attachment. Initially, I saved it with the intention of reviewing it later and added it to my "TO DO List." However, as other tasks took precedence, it gradually slipped down the queue. Just a few days ago, I finally resolved to investigate the contents of that email and unravel its purpose.
Therefore, I proceeded to save the attachment and started examining its contents. As this was an .xls file, I looked at the “Details” pane under “Properties”.
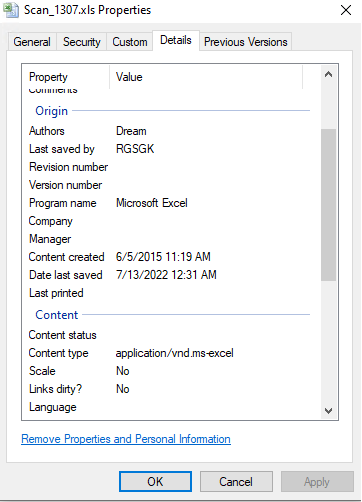
Values for “Authors” and “Last saved by” looked suspicious: “Dream” and “RGSGK”, so I grabbed them and did a quick search on Google.
First two results were already hinting towards something bad, and I knew there’s something worth investigating further:
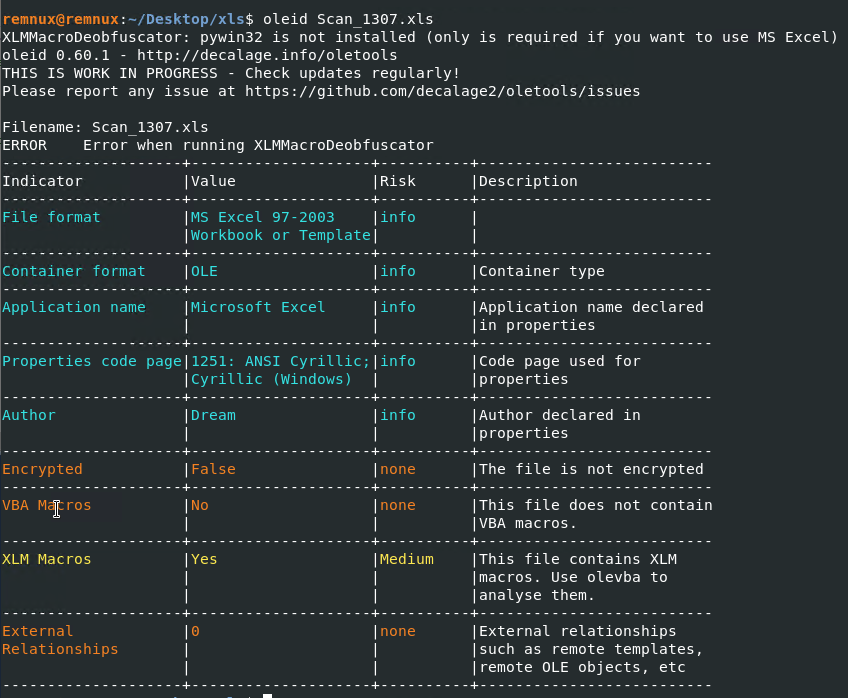
 Running oleid against the file revealed it contains XLM Macros:
Running oleid against the file revealed it contains XLM Macros:
Olevba also pointed out there’s an XLM Macro inside the file, but I just couldn’t extract it with any CLI tool.
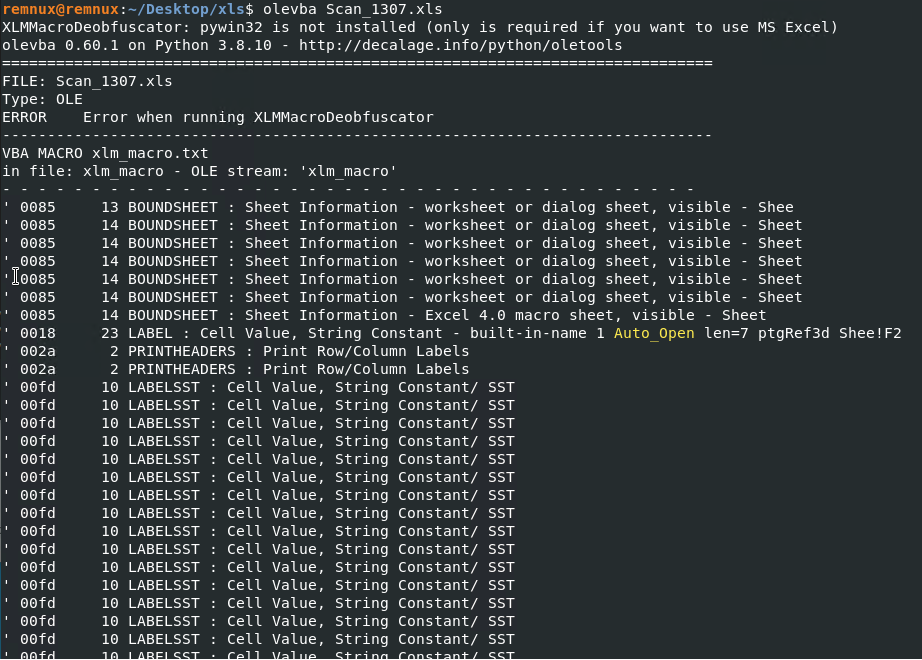
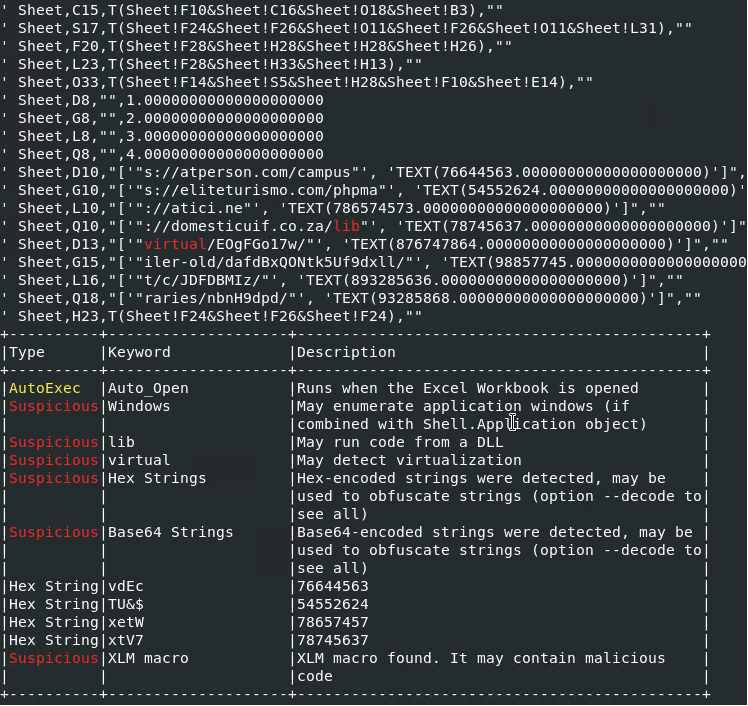
Instead, it revealed some interesting strings that looked like parts of urls, and at this point I decided to take a closer look at the file content.
Following the breadcrumbs and decrypting/deobfuscating the strings, I was able to extract a CALL on urlmon for function URLDownloadToFileA for some domains that proved to be malicious, according to VirusTotal.
Indicators of compromise:
hxxps://atperson[.]com/campusvirtual/EOgFGo17w/
hxxp://atici[.]net/c/JDFDBMIz/
hxxps://eliteturismo[.]com/phpmailer-old/dafdBxQONtk5Uf9dxll/
hxxp://domesticuif[.]co[.]za/libraries/nbnH9dpd/
Unfortunately, all the links were dead at the time I was conducting my investigation, so I had to search for those indicators online, maybe someone else stumbled upon them.
I ended up finding the dll that’s supposed to be downloaded (I took the latest one provided by urlhaus):
I also found some analysis reports on JoeSandboxCloud for this specific sample. Unfortunately the extracted configuration didn’t match, although it was the same sample: version1 and version2.
At this point I already knew that Emotet was the malware family delivered by this malicious XLS downloader, and although the IOCs extracted would be enough to alert and block at the edge router/firewall in order to protect the perimeter, an in-depth analysis of the DLL containing Emotet would reveal the C2 indicators. But that’s a topic for a part 2 of this article.
Final thoughts
To counter the growing threat of phishing emails, organizations must prioritize cybersecurity awareness and education among their employees, as vigilance is key!
Robust email filtering systems, multi-factor authentication, and regular security audits are vital components of a comprehensive defense strategy. By cultivating a culture of attentiveness, promoting best practices, and investing in advanced security technologies, organizations can strengthen their resilience and effectively mitigate the risks posed by phishing attacks.






