What is GuardDuty?
GuardDuty is a threat detection service offered by Amazon Web Services (AWS) that continuously monitors and analyzes network activities, account behaviors, and AWS infrastructure configurations for potential security threats and violations. It uses machine learning algorithms, anomaly detection, and integrated threat intelligence to identify suspicious activities and behaviors across AWS accounts, workloads, and data stored in AWS. GuardDuty can detect a wide range of threats including unauthorized access, privilege escalation, data exfiltration, malware infections, and reconnaissance activities. It provides security teams with real-time alerts and detailed findings to help them investigate and respond to security incidents quickly.
Why do you need GuardDuty?
GuardDuty continuously monitors and detects threats to our AWS accounts and workloads, we require it. It aids in spotting potentially malicious behavior or unauthorized access attempts and alerts security professionals to look into and address such situations as soon as possible. GuardDuty contributes to improving our AWS environment's security posture by increasing insight into potential security issues and assisting in ensuring compliance with security best practices and legal requirements. GuardDuty helps us proactively discover and fix security problems, lowering the possibility of security breaches and data loss.
How does GuardDuty work?
GuardDuty helps you access built-in detection techniques developed and optimized for the cloud. AWS Security continuously maintains and improves these detection algorithms.
![]()
The primary detection categories include:
-
Reconnaissance: Activity suggesting reconnaissance by an attacker, such as unusual API activity, suspicious database login attempts, intra-VPC port scanning, unusual failed login request patterns, or unblocked port probing from a known bad IP.
-
Instance compromise: Activity indicating an instance compromise, such as cryptocurrency mining, backdoor command and control (C&C) activity, malware using domain generation algorithms (DGA), outbound denial of service activity, unusually high network traffic volume, unusual network protocols, outbound instance communication with a known malicious IP, temporary Amazon EC2 credentials used by an external IP address, and data exfiltration using DNS.
-
Account compromise: Common patterns indicative of account compromise include API calls from an unusual geolocation or anonymizing proxy, attempts to disable AWS CloudTrail logging, changes that weaken the account password policy, unusual instance or infrastructure launches, infrastructure deployments in an unusual region, and API calls from known malicious IP addresses.
-
Bucket compromise: Activity indicating a bucket compromise, such as suspicious data access patterns indicating credential misuse, unusual Amazon S3 API activity from a remote host, unauthorized S3 access from known malicious IP addresses, and API calls to retrieve data in S3 buckets from a user with no prior history of accessing the bucket or invoked from an unusual location. GuardDuty continuously monitors and analyzes AWS CloudTrail S3 data events (e.g. GetObject, ListObjects, DeleteObject) to detect suspicious activity across all of your Amazon S3 buckets.
Pricing
There is a 30-day free trial for GuardDuty. Pricing for GuardDuty changes from region to region. After the trial period ends, GuardDuty prices are based on the volume of both analyzed service logs and data scanned for malware. The pricing for GuardDuty is pretty consistent across the US regions. To get more details on pricing for each region, please refer to the Link to GuardDuty Pricing.
The picture attached below illustrates the pricing for the region of US East Ohio.
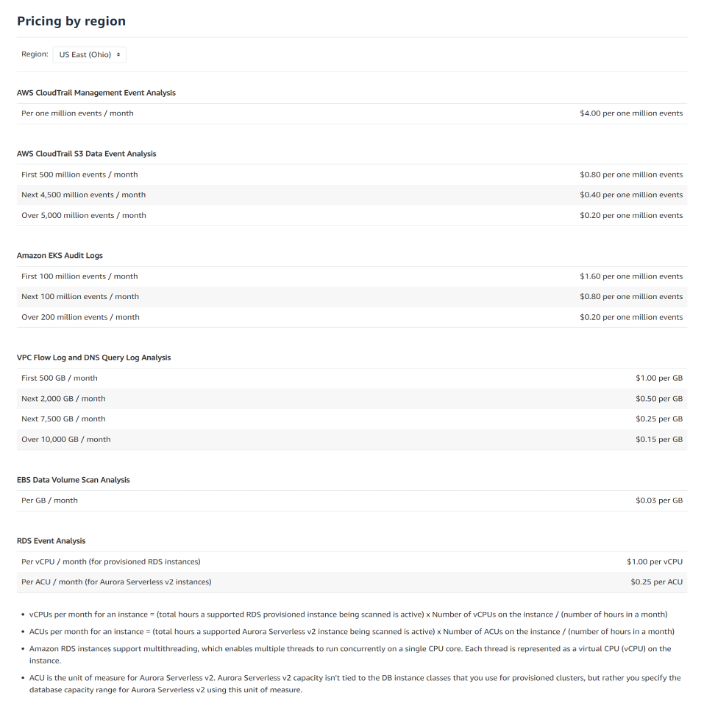
Some examples of pricing for different management events volumes:
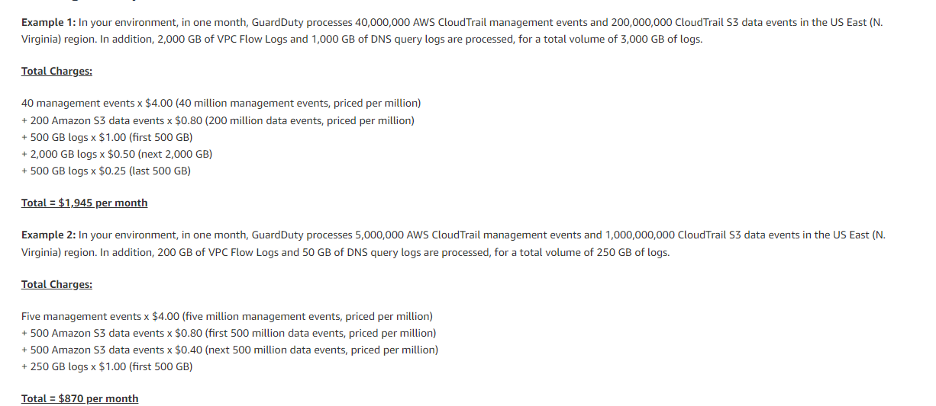
You can estimate the price of GuardDuty using different scenarios, such as the ones above, with the help of the AWS Pricing calculator. Please make sure to choose the region for which you want to check the costs.
Ways to minimize pricing of GuardDuty
-
Use a free trial: AWS offers a 30-day free trial of GuardDuty, which you can use to evaluate the service before committing to it.
-
Choose the right detection level: Choose the detection level that meets your organization's needs. This will help you avoid paying for features you don't need.
-
Review and tune your GuardDuty settings regularly: This can help you identify and fix issues that may be costing you money.
-
Use custom threat intelligence lists: By providing your own threat intelligence lists, you can reduce the number of findings generated by GuardDuty, which in turn can help reduce costs.
-
Use CloudWatch Events rules to filter out irrelevant findings: You can create CloudWatch Events rules to filter out findings that are not relevant to your organization. This can help reduce the number of findings generated by GuardDuty, which can help reduce costs.
-
Use resource groups: By using resource groups, you can limit the scope of GuardDuty to specific AWS accounts or regions, which can help reduce the number of findings generated and help reduce costs.
-
Enable data sampling: By enabling data sampling, you can reduce the amount of data that GuardDuty analyzes, which can help reduce costs.
-
Use Reserved Instances: If you plan to use GuardDuty for an extended period, you can consider purchasing Reserved Instances to save costs.
-
Set up cost alerts: You can set up cost alerts to monitor your GuardDuty spending and take action if costs exceed a certain threshold.
-
Choose the right AWS region: The pricing for GuardDuty varies by region, so make sure to select the region that offers the lowest pricing.
-
Use Amazon CloudWatch Events to monitor GuardDuty: This can help you reduce the number of notifications you receive, which can help lower costs.
How to import GuardDuty Findings in an S3 Bucket
To successfully configure the options for exporting GuardDuty findings to an S3 bucket, you need to meet certain prerequisites. In addition to having permissions to GuardDuty actions, you must have permissions for the following actions: kms:ListAliases, s3:CreateBucket, s3:GetBucketLocation, s3:ListAllMyBuckets, s3:PutBucketAcl, s3:PutBucketPublicAccessBlock, s3:PutBucketPolicy, and s3:PutObject. These permissions are essential for selecting a bucket to store findings and a KMS key for data encryption. Please refer to the section Granting GuardDuty permissions to a bucket and Granting GuardDuty permission to a KMS key from the AWS Document: Exporting findings.
When you configure the export of GuardDuty findings, you can choose an existing S3 bucket or have GuardDuty create a new bucket to store exported findings in. If you choose to use a new bucket, GuardDuty applies all necessary permissions to the created bucket. If you use an existing bucket, you must first update the bucket policy to allow GuardDuty to put findings into the bucket. You may also export findings to an existing bucket in another account.
To configure findings export using a new bucket
-
Add a policy to the KMS key that GuardDuty will use to encrypt findings. For example, policy, see Granting GuardDuty permission to a KMS key.
-
Open the GuardDuty console at https://console.aws.amazon.com/guardduty/.
-
Choose Settings.
a On the Settings page, under S3 bucket in the Finding export options section, choose Configure now.
b. Choose New bucket to create a new bucket to store exported findings. In the Name the bucket field, enter a name for the bucket. The name must be unique across all S3 buckets. Bucket names must start with a lowercase letter or a number.
c. If you used an [optional prefix] in your bucket policy you must enter that prefix under Log file prefix, otherwise this is optional. When you enter a value, the example path below the field is updated to reflect the path to bucket location where your exported findings will be stored.
d. Under KMS encryption, do one of the following:
-
Select Choose key from your account. Then choose the key alias of the key that you changed the policy for from the Key alias list.
-
Select Choose key from another account. Then enter the full ARN to the key that you changed the policy for. The key that you choose must be in the same Region as the bucket. To learn how to find the key ARN, see Finding the key ID and ARN.
e. Choose Save.
To configure findings export using an existing bucket
-
Add a policy to the KMS key GuardDuty will use to encrypt findings. For an example policy see Granting GuardDuty permission to a KMS key.
-
Attach a policy granting GuardDuty permission to upload objects to your S3 bucket. For an example policy see Granting GuardDuty permissions to a bucket.
-
Open the GuardDuty console at https://console.aws.amazon.com/guardduty/.
-
Choose Settings.
a. On the Settings page, under S3 bucket in the Finding export options section, choose Configure now.
b. Choose Existing bucket in your account. In the Name the bucket field enter the name of your bucket.
c. Optional. Under Log file prefix, enter a path prefix to use. GuardDuty will create a new folder in the bucket with specified prefix name. When you enter a value, the example path below the field is updated to reflect the path to exported findings in the bucket.
d. Under KMS encryption, do one of the following:
-
Select Choose key from your account. Then choose the key alias of the key that you changed the policy for from the Key alias list.
-
Select Choose key from another account. Then enter the full ARN to the key that you changed the policy for. The key that you choose must be in the same Region as the bucket. To learn how to find the key ARN, see Finding the key ID and ARN in the AWS Key Management Service Developer Guide.
-
e. Choose Save.
To configure findings export using an existing bucket in another account
-
Add a policy to the KMS key GuardDuty will use to encrypt findings. For an example policy see Granting GuardDuty permission to a KMS key.
-
Attach a policy granting GuardDuty permission to upload objects to the S3 bucket in another account. For an example policy, see Granting GuardDuty permissions to a bucket.
-
Open the GuardDuty console at https://console.aws.amazon.com/guardduty/.
-
Choose Settings.
a. Choose Existing bucket in another account.
b. In the Bucket ARN field, enter the ARN for the bucket from another account to use.
c. Under KMS encryption enter the full ARN of the key that you changed the policy for. The key you choose must be in the same Region as the bucket. To learn how to find the key ARN, see Finding the key ID and ARN.
d. Choose Save.
Note the following about export settings for findings:
-
Export settings are regional, which means you need to configure export options for each Region in which you're using GuardDuty. However, you can use the same bucket in a single Region as the export destination for each Region you use GuardDuty in.
-
Archived findings, including new instances of suppressed findings, aren't exported. If you unarchive a finding, its status is updated to Active, and it will be exported at the next interval.
-
If you enable findings export in a GuardDuty administrator account, all findings from associated member accounts that are generated in the current Region are also exported to the same location that you configured for the administrator account.
Learn more about how managed cloud detection and response (CDR) can protect your organization's cloud workloads and applications. Or, if your detection and response needs are more extensive, check out our comprehensive MXDR solution to see how Gradient Cyber MXDR can help protect all on-premises and cloud environments from cyber attacks.




.png?height=500&name=IAM%20Acces%20Analyzer%20(1365%20x%20768%20px).png)