Introduction
In the complex world of cybersecurity, where threats evolve with dizzying speed and complexity, the need for advanced, integrated defense systems has become paramount. Enter Managed Extended Detection and Response (MXDR), the multi-faceted shield designed to protect the modern enterprise from the onslaught of cyber attackers. For mid-market businesses, MXDR solutions can convert the chaos of network, endpoint, application, cloud and user behavior data into actionable, streamlined defense.
MXDR (Managed XDR) isn't just the latest security services buzzword. It's a managed detection and response capability that converges predictive intelligence, detection, response into an affordable service. It's a defense-in-depth layer that is really essential for businesses operating in a time where cyber threats don’t knock on the front door - they insidiously seep through every digital entry point.
This goal of this blog is to explain what MXDR (Managed XDR) is, how it works, the results it can deliver, and who can benefit from those results.
Read on to learn more about why MXDR (Managed XDR) is (at least in our opinion) a must-have security component for mid-market organizations.
MXDR (Managed XDR) - A Layman's Overview
In the ‘old days’, a straightforward antivirus program and a sturdy firewall could hold the line against common threats. Today, that’s akin to using a candle to light a highway. Your attack surface is much broader, and the threats are far more sophisticated. MXDR (Managed XDR) is analogous to the unveiling of the electric grid - a comprehensive, powerful, and dynamic solution built, as a service, to protect the modern enterprise’s path forward.
MXDR (Managed XDR) assumes the bad guys are either already in, or will get in. Of course, that is the central premise of every detection and response solution. They all exist because the entire secure industry came to understand - long ago - that a security strategy built around prevention alone - the old high walls and a moat perimeter model - is a goner.
MXDR (Managed XDR) - plain and simple - says, "Give me all of your security-related telemetry, I'll dump all that data into a rich filtration system of analytics, find the alerts that matter, contextualize them, have smart humans vet the work, and then output findings in either or both a report and an action that responds to the threat in some desired manner."
Easier said than done, but that's what it is.
MXDR (Managed XDR) is designed for organizations that recognize they can't do this alone - at least not well . They simply don't have the time, skill, platform and SOC to pull this off. Back to our electric grid analogy above - you 'could' build your own power plant (OK, with solar panels, you might get closer), or you could just get you power from a local electric utility that does it day in and day out at scale. There are just clear cases in nature where outsourcing is the answer. In our judgment, threat detection and response is one of them. Looks like Gartner agrees - they predict that by 2025, 50% of organizations will use MDR services for threat monitoring, detection and response functions.
Oh, and in case you're wondering if MDR and MXDR (Managed XDR) are one and the same - no they are not. Many buyers think MDR is largely based upon Managed EDR (MEDR). MXDR is far more comprehensive. To get a little more insight into that topic, check out this related blog.
How MXDR (Managed XDR) Works
Let's get to the specifics. Here's a snapshot (it's ours, of course, but conceptually it's representative of each key element of - hopefully - any MXDR (Managed XDR) solution). It shows how things flow from front-end data ingestion on the left all the way to the endgame of response and remediation on the right:
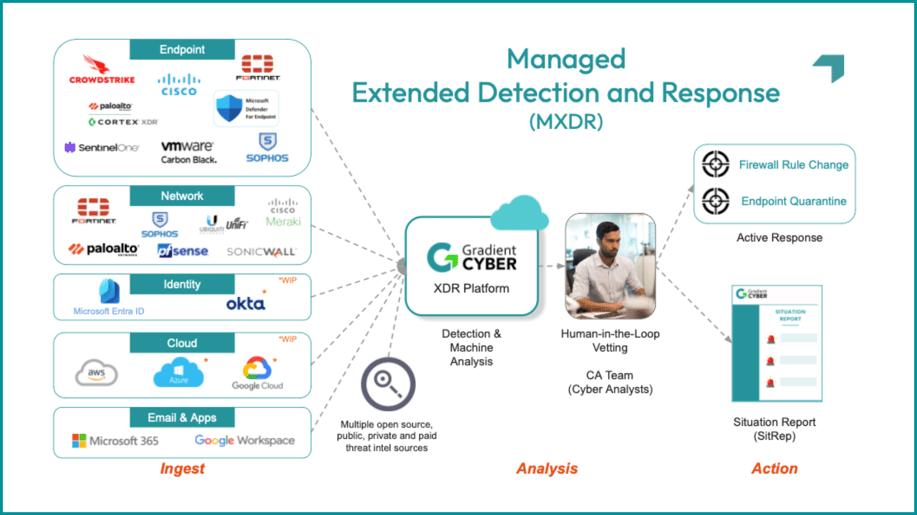
The Mechanisms of MXDR
At its core, a MXDR (Managed XDR) service is a fusion of advanced technology and seasoned expertise. If you want it short and sweet, the diagram above shows that MXDR does five things:
- It plugs in to your existing security stack
- Alerts, logs, traffic flow data, threat intel, etc. are ingested into an XDR platform
- AI and human analytics correlate, contextualize and prioritize events
- Security analyst staff produce SitReps
- Active or passive corrective action is taken, depending on your stack and service options
But if you read this far, you’re probably in pursuit of a bit more detail. Let's break down the requisite components a little further:
Broad, Agnostic Security Telemetry
It starts with the meticulous collection and analysis of data across various domains - network, endpoints, applications, and users' behavior. Note one thing right away. Not all MXDR (Managed XDR) services are agnostic to data sources. There are loads of endpoint and firewall brands out there. Many MXDR (Managed XDR) solutions are either vendor-provided (and therefore force their particular brand of EDR or NGFW), or are from MDR service providers solely wedded to one vendor brand per data source type. Buyer beware.
Advanced Threat Analytics
An MXDR (Managed XDR) solution should be powered by sophisticated analytics that cross three domains:
- Baseline: statistical and threshold
- Advanced: protocol, heuristic, flow
- AI: unsupervised machine learning and predictive
Any MXDR (Managed XDR) service should have analytics that continuously evolve, learning from past threats to fortify against future incursions. Analytics - and especially AI-based analytics - are a deep topic. Too much to cover fully in this blog, but check out our companion blog on how we see AI changing MXDR in the near term for a bit more insight.
Threat Intelligence Augmentation
Threat intel feeds - and more than a few - are essential to keep an MXDR (Managed XDR) solution on the front line of identifying emerging threats and vulnerabilities in real-time. MXDR (Managed XDR) vendors should use as many sources as possible - even if it leads to overlap, which drives up data confidence. But regardless of the actual intel feed count, you at least want to be sure that the solution leverages intel from these camps:
- Open-source intelligence (OSINT): publicly available information from news articles, blogs, social media platforms, and security forums
- Information Sharing and Analysis Centers (ISACs): industry-specific (finance, healthcare, energy, etc.) organizations that share cyber threat information amongst members
- Commercial Threat Intelligence Providers: Free and paid sources that specialize in collecting, analyzing, and providing threat intelligence services
- DoD Threat Intel
Expert Analyst Vetting
While automation and machine learning are indispensable, for the foreseeable future it's best to control them with human-led vetting and analysis. A MXDR (Managed XDR) solution should have a team of cybersecurity experts capable of scrutinizing each and every alert of merit, ensuring that recommended actions are calibrated to the specific threat. This human oversight is vital in cutting through the noise of false positives and focusing on genuine threats. Again, we are all infatuated with AI. And the promise is both enormous, and improving by leaps and bounds every quarter. But you need an incredible faith model to believe false positives or negatives just drop to zero because AI can do more and more of what human analysts do. We aren't at AGI yet. Don't assume away human expertise.
Situation Reports Spell It Out
Situation Reports (SitReps) are more than just reports; they are comprehensive assessments that offer context, implications, and recommended actions. This level of detail transforms technical data into strategic knowledge, empowering decision-makers to understand and act on the security threats their business faces. Your MXDR (Managed XDR) solution provider should be fully capable of doing all response heavy lifting. But whether you choose active or passive response (next point below), you'll always need a document that gives you the 'tale of the tape'.
Active and Passive Responses
A worthy MXDR (Managed XDR) service should provide a balanced approach to threat response. Active responses go beyond SitReps, resulting in swift and decisive actions taken by the MXDR (Managed XDR) service provider to neutralize immediate threats. This could involve isolating infected endpoints, blocking suspicious network traffic, or deploying countermeasures against active attacks.
Passive responses end with a SitRep - which contains all necessary source alert and IOC information, contextual analysis, and recommended action(s), but leaves the final response steps in the hands of the customer, or in some cases, the customer's managed services partner.
This dual approach ensures maximum customer flexibility with respect to both security policies and automation frameworks.
What Security Threats Can MXDR (Managed XDR) Actually Find?
At the "news headline" level, MXDR (Managed XDR) finds evidence of mounting risk of, or an actual incident associated with, one or more of:
- Ransomware
- Phishing
- Business email compromise (BEC)
- Supply chain attacks
- Cloud security vulnerabilities
- Insider threats
- Internet of Things (IoT) vulnerabilities
- Distributed Denial of Service (DDoS)
- Advanced Persistent Threats (APT)
- Third-party risks
- Zero-Day Vulnerabilities
- Data Leakage and Loss
- Weak or Stolen Credentials
- Nation-state attacks
But what's really going on 'in the boiler room' is the discover of the indicators that underpin the above security incidents:
- Network Attack Signals
- Botnets
- DNS Anomalies
- Malware Signatures
- Unauthorized Port Scans
- Unusual Traffic Patterns
- Zero Day Exploits
- Unauthorized Peer-to-Peer Networks
- Phishing Attacks
- Unchecked TOR Communications
- Endpoint Attack Signals
- Installed Malware
- Zero Day Exploits
- Unauthorized Software Installation
- Privilege Escalation Attempts
- Unauthorized Group Modifications
- Identity Attack Signals
- Lateral Movement
- Password Change Thresholds
- Zero Day Exploits
- Account Anomalies
Now the above is a representative set, not a comprehensive set.
But the idea is to not only consume the telemetry that exposes one or more of those signals (again from an ocean of signals that in any mid-market business could easily number on the hundreds of thousands to millions PER DAY), but run them to ground.
That means exercising the aforementioned process of finding the signal, contextualizing it, prioritizing it, determining the best response action, performing the action, and finally reporting on it - so the organization can improve its security hygiene, policies, procedures, human awareness training, etc.
Alert in. Alert out. Day in. Day out.
It's the Results That Matter
Great. A lot of solution requirements (and scary bad things that an MXDR (Managed XDR) solution should be able to find). But as an end customer what you really should want is simply this:
- Reduced Mean Time to Detect (MTTD)
- Reduced Mean Time to Respond (MTTR)
- These two at lower cost
In a nut shell that's it. A capable MXDR (Managed XDR) service provides the above - and ultimately gives you security peace of mind. By offloading the complexity of cybersecurity to an MXDR (Managed XDR) provider, your business can focus on growth and innovation, secure in the knowledge that your digital assets are under vigilant protection.
Now, your business leaders probably don't wake up every day thinking about MTTD and MTTR. So when you need to explain the value to them in 'business speak', it comes down to:
24/7 Threat Monitoring and Response
The digital world never sleeps, and neither do cyber threats. MXDR (Managed XDR) services offer round-the-clock monitoring, ensuring that threats are not just identified but also responded to in real-time. This continuous vigilance means businesses can operate without the looming anxiety of unaddressed vulnerabilities or latent attacks. By converting mountains of logs, alerts, and threat intelligence into clear action, MXDR (Managed XDR) cuts through the noise, relieving businesses of alert fatigue. Expert analysts do the heavy lifting, discerning the real threats from false alarms, and ensuring that each incident is met with the appropriate response.
Your Own SOC Without the Headaches
Building and maintaining a Security Operations Center (SOC) is a resource-intensive endeavor, often beyond the reach of many mid-market businesses. A MXDR (Managed XDR) service should provide the benefits of a fully-functional, certified SOC without the associated overhead. This offering includes access to the latest in cybersecurity technologies and skilled analysts, eliminating the need for extensive investment in training or infrastructure. For businesses grappling with the challenge of finding, hiring, and retaining cybersecurity talent, SOC-as-a-service is a game-changer.
Cutting Edge Security Intel and Technology
In the ever-evolving landscape of cyber threats, staying current is not just an advantage - it’s a necessity. An MXDR (Managed XDR) service integrates a multitude of threat intel feeds, ensuring that its security measures are always ahead of the curve. The service is underpinned by a blend of unsupervised machine learning and human insight, ensuring threat detection and response capabilities are always evolving and adapting to the latest threat scenarios.
Preventing IT Staff Burnout and Turnover
IT teams are the unsung heroes of the digital business world, often juggling a plethora of tasks to keep operations running smoothly. Adding the burden of comprehensive cybersecurity can push these teams to their limits. A MXDR (Managed XDR) service offloads this burden, allowing IT staff to focus on driving business resilience and growth. This not only enhances productivity but also contributes to better staff retention by reducing burnout.
Compliance Assurance Across Industry Standards & Frameworks
Navigating the complex web of industry standards and compliance frameworks is a daunting task for any business. A good MXDR (Managed XDR) service provider will also offer NIST 800-171 and CMMC 2.0 security assessments that help align your security measures with best practices, simplifying compliance with regulations across a variety of standards including FERPA, COPPA, HIPAA, HITECH, GLBA, SOX, PCI DSS, FISMA, CAT, TCF, and IMO.
Big Cost Savings
In the calculus of cybersecurity, prevention alone is insufficient; while detection and response are crucial. Building an in-house SOC, however, is a costly and time-consuming endeavor. By outsourcing to a MXDR (Managed XDR) provider, businesses can avoid the high costs and logistical challenges associated with establishing an internal SOC. This shift not only represents a significant cost saving, it also ensures access to a level of expertise and technology that might otherwise be unattainable.
Who Needs MXDR (Managed XDR)?
Here's the acid test question: Does your organization have a bank account, intellectual property, or any customer or employee data?
If yes, you probably need to take a hard look at MXDR (Managed XDR).
But that may come across as 'too obvious'. So taken a step deeper, the real drivers for MXDR (Managed XDR) hold true regardless of organization size, cybersecurity maturity, business vertical, or depth of security stack. Consider these three points,:
- The amount of data you need to ingest, process, and analyze to find the proverbial 'needle in the haystack' is astronomical. The attackers could very well be in your IT environment right now. The footprints and broken branches are likely there to prove it. But where do you start?
- The attackers are really good at what they do. They are highly-skilled, well-tooled, and extremely motivated. And they are way more of them than you have on your IT /security team.
- Unless your company is in the "security 1%", your IT staff cannot keep up. They are somewhere between overwhelmed and burned out.
These issues are especially difficult for mid-market businesses, each with a unique set of challenges and goals:
On one end of the spectrum, we see mid-market businesses typified by an IT Manager juggling multiple roles (including security), but without extensive formal training in cybersecurity. The primary challenge here is in navigating the complex world of cyber threats with limited resources and expertise. They just want someone to make the security pain go away - allowing them to focus on critical IT work just to keep the business running.
At the other end, we see organizations who are fairly mature in their understanding of cybersecurity, and have relatively sophisticated defense-in-depth security stacks. However, while less challenged by cybersecurity expertise, they are tapped out by a sea of other responsibilities.
A good mid-market MXDR (Managed XDR) service should easily adapt to the varied hues of mid-market organizations - from entities with less cybersecurity skill and experience to those with more cybersecurity expertise but insufficient bandwidth to do the work of threat detection and response.
Conclusion
MXDR (Managed XDR) is, in our judgement, essential for every business - but especially for mid-market organizations who will struggle to stay ahead of attackers due to the near impossibility of being able to staff, equip and keep an XDR solution - a vital component of the modern security stack - up and running properly and effectively. The attackers are there. They are relentless, smart, well-tooled and highly motivated. Are you really going to go it alone?
Our goal with this blog is just to inform you about MXDR (Managed XDR) at large. Of course we are proud of our solutions, and want to encourage you to take a look at what we have to offer. If you'd like to know more about our MXDR (Managed XDR) solution and the benefits we provide, check out our solution page. If you're curious about what makes Gradient Cyber stand out, we've captured that on our Why Gradient Cyber page. Or, if you just have a question, reach out to us - either via our chatbot on the homepage, or via one of our forms. Hey, in this virtual world, we do love the chance to actually talk to people :-).