What is IAM?
AWS Identity and Access Management (IAM) is a service that helps you securely control access to AWS resources. With IAM, you can centrally manage permissions that control which AWS resources users can access. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources. To learn more about IAM please refer to the documentation on How IAM works.
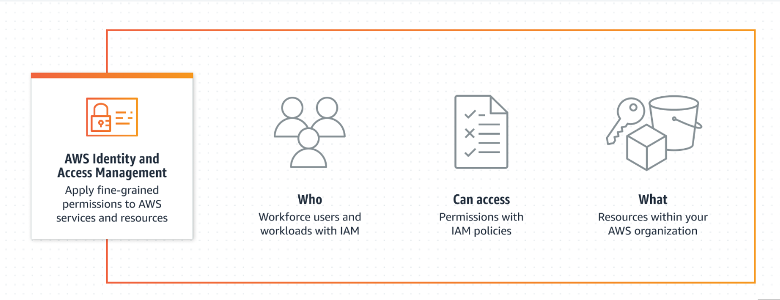
Why do you need IAM?
IAM helps to bring security value to monitoring in AWS by providing a secure and centralized way to manage access to resources, track user activity, and enforce security policies.
What can you do with IAM?
Quite a few things:
-
Continually analyze access to right-size permissions on the journey to the least privilege.
-
Provides Shared access to your AWS account and uses resources in your AWS account without having to share your password or access key.
-
Allows you to enable two-factor authentication to your account and individual users for extra security.
For more in-depth details and other useful features of IAM, please refer to the Documentation by AWS.
Why do you need an alerting system for IAM?
An alerting system is important for Identity and Access Management (IAM) because it can help to identify and mitigate security risks in a timely manner. Any unauthorized access or suspicious activity can pose a significant threat to an organization's security posture. It is important to monitor user activity and generate alerts when certain events occur, such as multiple failed login attempts or unusual access patterns. This can help security teams quickly identify and respond to potential security incidents before they can cause damage.
-
Brute force attacks can compromise security: If successful the attacker can gain access to sensitive data or resources. By setting up alerts on CloudTrail logs, you can detect these attacks and take action to prevent them from succeeding.
-
Alerts can help you respond quickly: Alerts get deployed in real-time, this can help you respond quickly and take appropriate action, such as locking down affected accounts, resetting passwords, or blocking IP addresses.
-
Alerting can help you identify patterns: By analyzing CloudTrail logs and setting up alerts, you can identify patterns of brute force attacks. This information can help you take steps to prevent future attacks.
-
Alerting can help you meet compliance requirements: Many compliance frameworks require organizations to monitor suspicious activity, including brute force attacks. By setting up alerts in CloudTrail, you can meet these requirements and demonstrate that you are taking security seriously.
Costs for using services in IAM? Nothing.
There is no additional charge for creating additional users, groups, or policies in IAM.
AWS Identity and Access Management (IAM) and AWS Security Token Service (AWS STS) are features of your AWS account offered at no additional charge. You are charged only when you access other AWS services using your IAM users or AWS STS temporary security credentials. For information about the pricing of other AWS products, see the Amazon Web Services pricing page.
Costs for implementing the alerting system for IAM
Costs for this alerting system would entail the usage of IAM together with the AWS Cloud services: CloudTrail, CloudWatch, and SNS.
The AWS Free Tier provides customers the ability to explore and try out AWS services free of charge up to specified limits. The Free Tier quota for the below would include:
-
CloudWatch
-
10 Custom Metrics and 10 Alarms
-
1,000,000 API Requests
-
5GB of Log Data Ingestion and 5GB of Log Data Archive
-
3 Dashboards with up to 50 Metrics Each per Month
-
-
CloudTrail
-
Free - View, filter, and download the most recent 90 days of your account activity for all management events in supported AWS services.
-
Free - Set up a trial that delivers a single copy of management events.
-
-
SNS
-
1,000,000 Publishes
-
100,000 HTTP/S Deliveries
-
1,000 Email Deliveries
-
Costs exceeding the Free Tiers limits depend on the usage of the services and can be calculated via AWS Pricing Calculator. Please cross-check the pricing for the services which are correlated with IAM.
Prerequisites for implementing your first alert
Requirements would entail having IAM, CloudTrail, CloudWatch, and Amazon Simple Notification Service (SNS) set up and having proper access to these services across all regions.
The inner workings of the alerting system
An alerting system typically works by continuously monitoring specified data sources for events that meet specific criteria. When an event matches the defined criteria, the alerting system triggers an alert, which can be in the form of an email, text message, or other notification. The goal of the alerting system is to provide timely notification to the appropriate parties so that they can take action to resolve any issues or address any potential threats.
Here’s how it works!
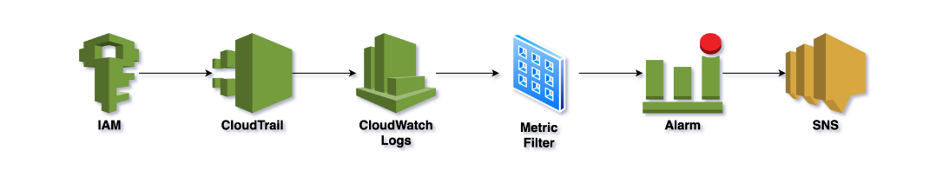
-
CloudTrail is continuously logging all AWS activity, including login attempts, to CloudWatch Logs.
-
A metric filter in CloudWatch Logs is continuously looking for patterns in the log that indicate failed login attempts.
-
When the filter finds a match, it increments the count of a custom metric we created.
-
When the metric crosses a threshold, we get an alarm!
For more information see Receiving Alerts When Your IAM Configuration Changes and Creating CloudWatch alarms for CloudTrail events: examples.
Learn more about how managed cloud detection and response (CDR) can protect your organization's cloud workloads and applications. Or, if your detection and response needs are more extensive, check out our comprehensive MXDR solution to see how Gradient Cyber MXDR can help protect all on-premises and cloud environments from cyber attacks.


.png?height=500&name=IAM%20Acces%20Analyzer%20(1365%20x%20768%20px).png)
.png?height=500&name=Identity%20Access%20Management%20(1365%20x%20768%20px).png)